Why Should I Care?
Advertisers constantly gather information about the sites you browse, services you use and even places you visit while you’re walking around with your phone. They do this for a number of reasons including providing a more personalized experience, say, showing you advertisements that are relevant to your interests. We unconsciously trade our personal information for more comfortable service experiences.Some of this may be fairly benign, but on some level, having anonymous companies gathering large volumes of data about you to create a consumer profile can be concerning. Further, this information is bought and sold, without you giving explicit approval or control over what is included. For this reason, taking an interest in your online security and privacy is important.
Aside from advertisers, you also have to be aware that there are people who will try to steal or take advantage of your personal information. For instance, if you use the same password for both your Gmail account and your Amazon account, which you really shouldn’t, and someone gets hold of your Gmail password, they can suddenly start placing Amazon orders under your identity. If you post that you’re going for vacation, publicly to Facebook, what’s to stop someone from unlawfully entering your residence while you’re out of town?
There are a number of things you can do to start taking control of your online identity. Securing your web browser is a great first step. Proper password practices and controlling what you store and share online, through internet services should be the next place to look.
Securing Your Web Browsing
1) Use a Virtual Private Network (VPN): This will mask your Internet (IP) address and encrypt traffic between you and your VPN host. To the outside world, it will look like any traffic requests are coming from your VPN host, instead of your computer. Why do this? Number one for me: online privacy. Companies like Google and Facebook connect all sorts of information about what you do online and can in many cases link it back to your IP address and browser fingerprint. Why let them gather all this information on you? TorrentFreak is a good place to research the right VPN for you. As an aside, you can also use VPNs to get around geographical blocks for certain services, though sites like Netflix went on a tear, blocking VPNs a while back for this very reason. A caveat with all this is that VPNs will add overhead to your internet connection, likely slowing things down, so you won’t necessarily want to leave them running all the time.
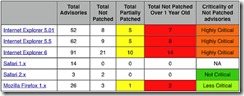
2) Secure your web browser: Update Chrome/Firefox/Microsoft Edge. After that, install plug-ins such as Ghostery, uBlock Origin (for Chrome, for Firefox) and HTTPS Everywhere to limit how easily advertising companies can collect information n on your browsing habits and secure your browsing. Also, by keeping your browser up-to-date, you mitigate known vulnerabilities, keeping you and your information safer.
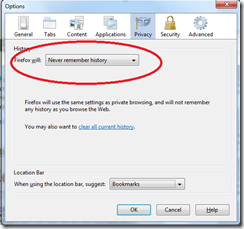
3) Use data silos: Sites like Facebook will not only track what you do on their site, but track activity in all other tabs in the browser running Facebook. Why let them gather information on you? By using a browser, say FireFox exclusively for Facebook, and another browser like Chrome for your other browsing, you limit what Facebook can collect. Way back when, I used to use a program called Sandboxie that would effectively limit applications from modifying / interfering with my host operating system. If you’re concerned about malware, in e-mail attachments for instance, running your e-mail client in a sandbox can help mitigate damage.
Maintain Your Passwords
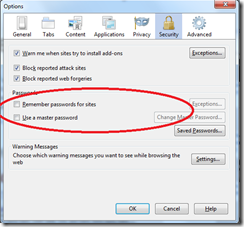
1) Site specific passwords: Use site / service unique passwords, and further, if you can, use a different log-in name than your e-mail address for any sites you use. The benefit of this is that, should one of your sites be compromised, the rest of your online identity won’t fall like a house of cards. Having site specific passwords can be a pain if you’re managing this bit manually, which I wouldn’t. Check out services like LastPass, which will not only manage your passwords, but back them up securely, make them available across all your devices and even generate extremely complex passwords for the sites you use. This will dramatically decrease the probability of having all your accounts compromised, should one of your sites get hacked.
2) Update your more sensitive site passwords regularly. Sites like your e-mail account and banking site should have their passwords changed periodically. Should your password become compromised at some point, by updating your password, the potential harm caused can be minimized.
Floating Through the Cloud
Ah jargon. I’ll not rant about the term, but basically, if you’re storing content online, make sure it doesn’t have sensitive personal information. If you wouldn’t leave tax documents sitting out in the open at the office, I wouldn’t leave tax documents unencrypted on someone else’s server. As such, be aware of what information you’re placing online. I use a no longer supported application called TrueCrypt (7.1a), which encrypts my more sensitive information, prior to uploading it. This application is no longer supported, however. VeraCrypt might be worth checking out, as an alternative.
Social Media Management
Share the minimum amount of personal information possible. If I’m going on vacation, I’ll only post about it afterwards. No reason to send thieves to my door. Be cognizant of what you’re sharing and always ask yourself, should this be online? Things like your Social Insurance Number, home address, and yes even your telephone number should not be easily publicly accessible. It’s much easier to mindlessly overshare than it is to permanently remove this information after the fact.
Advanced: Two-Factor Authentication
Passwords can be compromised and to combat this, some services allow an added level of security through what’s called two-factor or multi-factor authentication. The idea behind this is simple: to login to an account, you will need two bits of information. You need something you know, such as your account password, and something you have, which can be your cell phone to either generate a second secure code for log-in, or receive a securely generated code to log-in. This helps prevent unwanted access to your account, given the “something you have” piece, is presumably something only you have access to. Many services like Google’s gmail, Steam and Dropbox all support this level of security. It does add a bit of overhead, but adds additional confidence that only you can access your account.
Summary
By taking some of these steps, you can limit some of the information that is gathered about you and increase security of your information. The most onerous of these moves would be switching to a password manager and switching all your passwords, though in the long run it’s absolutely worth the hassle. Always be aware of what you’re sharing online and really consider whether you should be posting it online.
Header image by Krysten Newby // CC BY 2.0